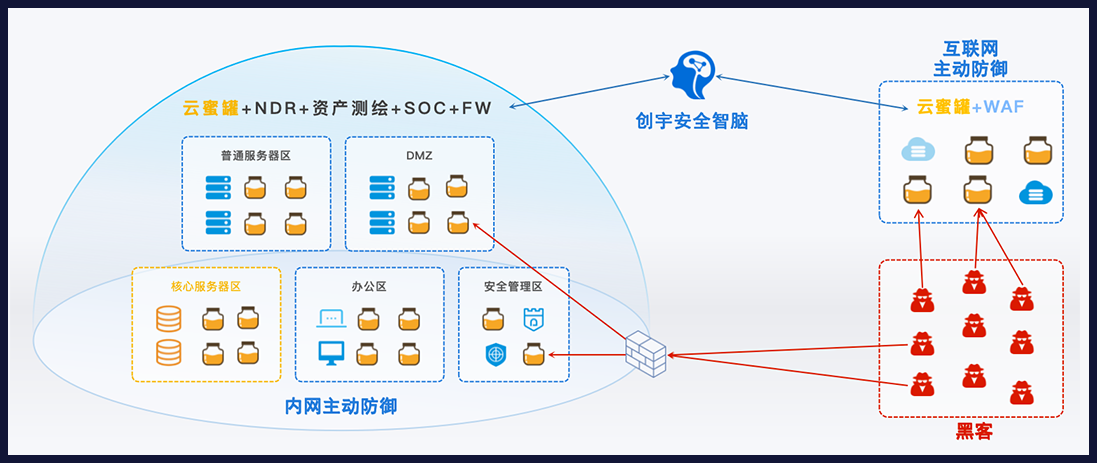
Cloud honeypot
Pioneering cloud honeypot domain access technology, this technology supports one click resolution of customers' domain names to cloud honeypot IP, allowing customers to deploy a large number of cloud honeypots in a short period of time and at low cost.
Attack tracing
Pioneering cloud honeypot domain access technology, this technology supports one click resolution of customers' domain names to cloud honeypot IP, allowing customers to deploy a large number of cloud honeypots in a short period of time and at low cost.
Automatic blocking
Pioneering cloud honeypot domain access technology, this technology supports one click resolution of customers' domain names to cloud honeypot IP, allowing customers to deploy a large number of cloud honeypots in a short period of time and at low cost.
Custom honeypot
Pioneering cloud honeypot domain access technology, this technology supports one click resolution of customers' domain names to cloud honeypot IP, allowing customers to deploy a large number of cloud honeypots in a short period of time and at low cost.
Network wide attack perception
Pioneering cloud honeypot domain access technology, this technology supports one click resolution of customers' domain names to cloud honeypot IP, allowing customers to deploy a large number of cloud honeypots in a short period of time and at low cost.
AD domain simulation technology
Pioneering cloud honeypot domain access technology, this technology supports one click resolution of customers' domain names to cloud honeypot IP, allowing customers to deploy a large number of cloud honeypots in a short period of time and at low cost.
Visualization technology
Pioneering cloud honeypot domain access technology, this technology supports one click resolution of customers' domain names to cloud honeypot IP, allowing customers to deploy a large number of cloud honeypots in a short period of time and at low cost.
Automatic intelligent response technology
Pioneering cloud honeypot domain access technology, this technology supports one click resolution of customers' domain names to cloud honeypot IP, allowing customers to deploy a large number of cloud honeypots in a short period of time and at low cost.
Security reinforcement technology
Pioneering cloud honeypot domain access technology, this technology supports one click resolution of customers' domain names to cloud honeypot IP, allowing customers to deploy a large number of cloud honeypots in a short period of time and at low cost.
Collaborative linkage technology
Pioneering cloud honeypot domain access technology, this technology supports one click resolution of customers' domain names to cloud honeypot IP, allowing customers to deploy a large number of cloud honeypots in a short period of time and at low cost.
Massive network security big data support
Pioneering cloud honeypot domain access technology, this technology supports one click resolution of customers' domain names to cloud honeypot IP, allowing customers to deploy a large number of cloud honeypots in a short period of time and at low cost.
Threat intelligence support
Pioneering cloud honeypot domain access technology, this technology supports one click resolution of customers' domain names to cloud honeypot IP, allowing customers to deploy a large number of cloud honeypots in a short period of time and at low cost.